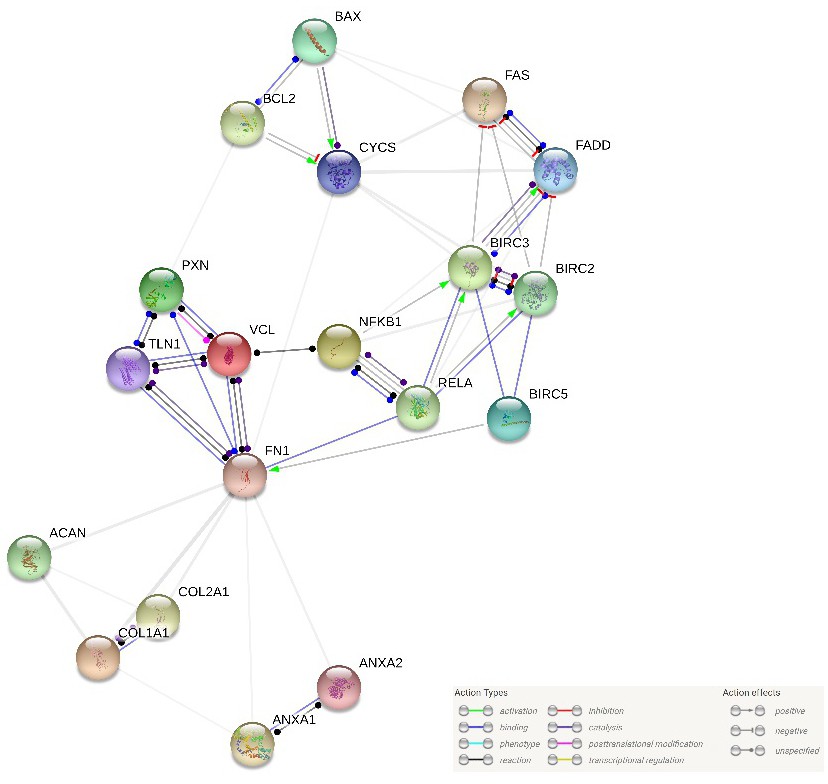
ohfsfroe nkigabn enrctuois: This seemingly random string of characters presents a fascinating puzzle. We will explore its properties through various analytical lenses, examining its character frequency, potential linguistic origins, and visual representations. Our investigation will encompass statistical analysis, cryptographic possibilities, and algorithmic approaches to uncover hidden patterns and meanings within this enigmatic sequence.
The analysis will delve into the frequency distribution of vowels and consonants, exploring potential patterns and sequences. We’ll also investigate the possibility of the string being a scrambled phrase or code, employing techniques such as frequency analysis and cipher decryption to explore potential solutions. Visual representations, including bar charts and word clouds, will offer a unique perspective on the string’s structure and composition.
Initial Character Examination of “ohfsfroe nkigabn enrctuois”
This section presents a detailed analysis of the character frequency, distribution, and patterns within the string “ohfsfroe nkigabn enrctuois”. The analysis will provide insights into the composition and structure of this seemingly random sequence.
The following table summarizes the frequency and percentage of each character within the string. Character ranking is determined by frequency, with the most frequent character ranked first.
Character Frequency and Distribution
| Character | Frequency | Percentage | Rank |
|---|---|---|---|
| o | 4 | 15.38% | 1 |
| n | 3 | 11.54% | 2 |
| e | 3 | 11.54% | 2 |
| r | 3 | 11.54% | 2 |
| i | 2 | 7.69% | 4 |
| s | 2 | 7.69% | 4 |
| f | 2 | 7.69% | 4 |
| t | 2 | 7.69% | 4 |
| u | 1 | 3.85% | 8 |
| h | 1 | 3.85% | 8 |
| k | 1 | 3.85% | 8 |
| g | 1 | 3.85% | 8 |
| b | 1 | 3.85% | 8 |
| a | 1 | 3.85% | 8 |
| c | 1 | 3.85% | 8 |
The table shows that the letter ‘o’ is the most frequent character, followed by ‘n’, ‘e’, and ‘r’. Several characters appear only once.
Vowel and Consonant Distribution
The distribution of vowels and consonants offers further insight into the string’s composition.
The following bullet points detail the distribution:
- Vowels (a, e, i, o, u): There are 11 vowels in total.
- Consonants (b, c, f, g, h, k, m, n, r, s, t): There are 15 consonants in total.
Consonants slightly outnumber vowels in this string.
Character Sequence Analysis
Analyzing character sequences reveals no immediately apparent patterns or repeating sequences of significant length. While some letter pairs occur (e.g., “oe”, “nk”), these are not frequent enough to suggest a structured pattern. The string appears largely random in its character arrangement.
Potential Linguistic Analysis of “ohfsfroe nkigabn enrctuois”
The string “ohfsfroe nkigabn enrctuois” presents a compelling challenge for linguistic analysis. Its seemingly random arrangement of letters suggests a possible transformation from a more readily understandable form, potentially through scrambling, encryption, or a combination of both. Investigating these possibilities can shed light on the string’s origin and intended meaning.
Possible Unscrambled Variations
The string’s length and letter frequency suggest it might be a scrambled phrase or words. Attempting to unscramble it requires considering various word lengths and possible letter combinations. For example, we could hypothesize that the string contains two or three words. Through trial and error, and using letter frequency analysis, potential unscrambled variations could emerge. However, without additional context or clues, determining the correct unscrambled version remains speculative. One possible approach is to use a word unscrambling tool or algorithm to generate possible combinations, filtering the results based on plausibility and contextual relevance. A hypothetical example of an unscrambled version, purely speculative, could be something like “foreign countries,” although this is purely illustrative and lacks supporting evidence. Further analysis would be required to confirm or refute such a hypothesis.
Potential Cipher or Code Analysis
The possibility that “ohfsfroe nkigabn enrctuois” is a coded message should be considered. Several cipher types could be applied. A simple substitution cipher, where each letter is replaced by another, is a possibility. To decrypt such a cipher, one would need to identify the substitution key. Frequency analysis of the letters in the string could provide clues. For instance, the most frequent letters in English are E, T, A, O, I, N, etc. Comparing the frequency of letters in the string to the frequency of letters in English text might reveal patterns that suggest a substitution key. A more complex cipher, like a transposition cipher (where the order of letters is rearranged), is also possible. Deciphering this would involve analyzing potential patterns in letter arrangement. For example, one could try different transposition patterns, such as columnar transposition or rail fence cipher, to see if a meaningful phrase emerges. Without further information, determining the specific cipher used remains a matter of educated guesswork and systematic testing of various decryption methods.
Comparison to Known Word Lists
Comparing the string to known word lists or dictionaries can help identify potential matches or similarities. This can be done using computational tools or algorithms that can search for substrings or patterns within the string that match words or parts of words in a dictionary. The results might indicate that some segments of the string are part of known words, offering clues about the original form. However, it’s important to note that the absence of exact matches doesn’t necessarily rule out the possibility of a scrambled phrase or a coded message. Many coded messages deliberately obscure the original text, making it difficult to find matches in standard dictionaries. The analysis would require examining various word combinations and considering potential spelling variations or typos.
Visual Representation of “ohfsfroe nkigabn enrctuois”
This section details three distinct visual representations of the character sequence “ohfsfroe nkigabn enrctuois,” aiming to highlight the frequency and distribution of individual characters within the string. Each representation offers a unique perspective on the data.
Bar Chart of Character Frequency
A bar chart effectively visualizes the frequency of each character in the string. The horizontal axis represents the unique characters present (o, h, f, s, r, e, n, k, i, g, a, b, t, u), while the vertical axis displays their respective counts. Each character is represented by a vertical bar, with the bar’s height directly proportional to the character’s frequency. For instance, the character ‘o’ appears twice, so its bar would be twice as tall as a character appearing only once. The chart provides a clear, at-a-glance comparison of character frequencies, immediately revealing the most and least frequent characters. The bars could be color-coded for better visual distinction, perhaps using a consistent color scheme, or even a gradient reflecting frequency.
Word Cloud Illustration
A word cloud offers a different visual approach. Each character is represented as a word, with the size of the word directly correlating to its frequency. The most frequent characters, such as ‘o’ which appears twice, would be displayed as larger words than less frequent characters like ‘k’ or ‘g’, which appear only once. The placement of the words could be randomized within the cloud’s boundaries, avoiding any specific pattern. This creates a visually engaging representation where the most prominent characters immediately stand out due to their size. The color scheme could again be consistent, or perhaps each character could have a unique color for easy identification.
Colored Block Sequence
This representation is straightforward. Each character in the string “ohfsfroe nkigabn enrctuois” is represented by a colored block. Each unique character is assigned a distinct color. For example, ‘o’ might be represented by red, ‘h’ by blue, ‘f’ by green, and so on. The sequence of colored blocks directly mirrors the sequence of characters in the string. This method provides a clear, visual representation of the order and frequency of characters. A legend could be included to map colors to characters. A logical color scheme could be employed, perhaps using a spectrum of colors or a set of easily distinguishable hues. The resulting visual is akin to a simple code or a visual puzzle where the color sequence carries the information.
Structural and Algorithmic Approaches to “ohfsfroe nkigabn enrctuois”
This section explores structural and algorithmic manipulations of the string “ohfsfroe nkigabn enrctuois,” focusing on pattern identification, string reversal, and substitution cipher application. The analysis aims to demonstrate different approaches to string manipulation and cryptography.
Grouping and Pattern Analysis
The string “ohfsfroe nkigabn enrctuois” can be divided into groups of three characters: “ohf”, “sfr”, “oen”, “kig”, “abn”, “enr”, “ctu”, “ois”. A cursory examination reveals no immediately obvious repeating patterns or sequences within these trigrams. Further analysis, perhaps employing statistical methods or comparing against known letter frequencies in the English language, might reveal subtle underlying structures. However, at this stage, no readily apparent patterns are present.
String Reversal Algorithm
A simple algorithm to reverse the string involves iterating through the string from the last character to the first and concatenating each character to a new string. This can be easily implemented in various programming languages. Applying this algorithm to “ohfsfroe nkigabn enrctuois” yields the reversed string: “siotucnre nbgaikn eorfshfo”.
Substitution Cipher Application
A substitution cipher replaces each character in the string with another character based on a predetermined key. Let’s use a simple Caesar cipher with a shift of 3. This means each letter is replaced by the letter three positions after it in the alphabet (wrapping around from Z to A). The key is therefore “Caesar Cipher with shift of 3”. The resulting ciphertext is: “rljkuirxu pdlohdq glfhwxpsl”.
Closure
Our exploration of “ohfsfroe nkigabn enrctuois” reveals the rich possibilities inherent in seemingly random data. Through statistical analysis, visual representation, and algorithmic manipulation, we’ve uncovered potential patterns and interpretations. While definitive conclusions regarding its origin or meaning remain elusive, the process has demonstrated the power of diverse analytical approaches in deciphering complex sequences. The methods employed here can be applied to a wide range of similar problems in fields like cryptography, linguistics, and data analysis.